Published on: 2024-11-26 (updated on: 2024-11-29). 🔗 Permalink
What is mTLS (Mutual TLS)?
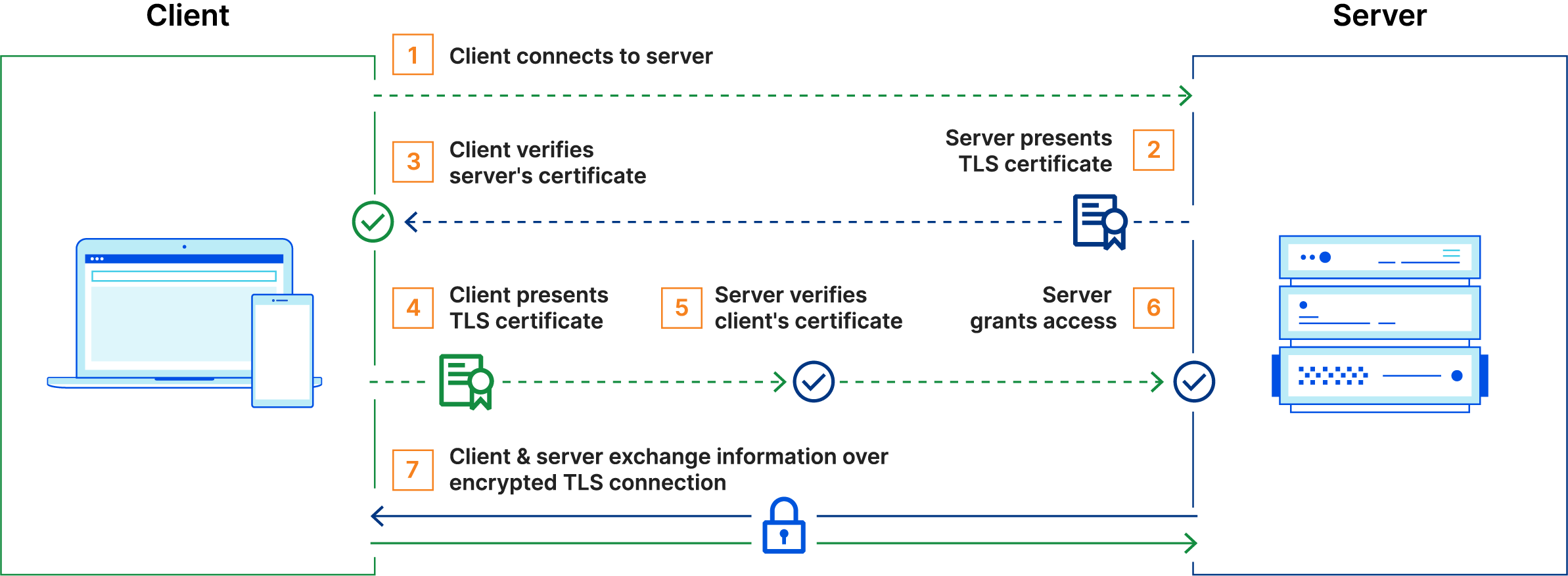
The instance of Ontoserver that is hosted through the SU-TermServ is protected using Mutual TLS. This means that with every access to the endpoint, a mutual certificate exchange takes place, so you need to set up a corresponding certificate on your side and present it with every connection establishment:
The process of requesting a certificate is described here. Instructions on how to set up the certificate in browsers can be found here.
The SU-TermServ uses mTLS to enforce the contractual condition that access to the Ontoserver instances may only be made from Germany.
The validation of your certificate on our servers is performed by the reverse proxy. If your request is not permitted, the request will never reach the underlying service.
By shifting the validation to the application layer at level 7 of the ISO/OSI reference model (instead of at level 4 in the transport layer), we can differentiate whether an authentication is successful. Therefore, certificates are generally not required for OPTIONS and HEAD requests, and static assets can be retrieved without a certificate. If you encounter issues accessing our services, it is worthwhile to take a look at the transmitted headers of the HTTP(S) response. The validation result is transparently returned by the services in the header X-SUTS-TLS-Verification; the IP zone we assign you is communicated in the X-SUTS-IP-Zone header.
We also reserve the right to permanently block IP addresses in case of abusive usage.
Current situation with GÉANT and Sectigo (updated on 2024-12-16)
The DFN has announced that Sectigo has terminated its contractual relationship with the GÉANT consortium due to differences.
On December 13, 2024, DFN announced that a new contractual relationship has been established with the Greek provider HARICA as a transitional solution. More information can be found regularly updated on the DFN pages regarding the current situation and on the services offered by HARICA in particular. We will, of course, accept HARICA certificates for authentication as soon as more information is available.
It is no longer possible to request certificates through Sectigo.
The security of access to our services is not at any time compromised by this changeover. We will inform about further steps through the channels of the coordination office and on this website.