Published on: 2024-11-26. 🔗 Permalink
Firefox shows blank pages
When using Mozilla Firefox, applications like Shrimp, Snapper, or OntoCommand may be unable to access the FHIR resources. In Shrimp, the page framework loads, but no content is displayed. In OntoCommand, either a blank page is shown or the application fails to load. This behavior does not occur with Chromium-based browsers.
The background of this behavior is a different handling of Mutual TLS authentication used by the SU-TermServ, in conjunction with the Cross-Origin Resource Sharing (CORS) mechanism [Mozilla Developer Network].
The CORS mechanism ensures that frontends can access resources hosted on another server from the backend. The frontend sends a request to the server that provides the resources. This server checks the request and decides whether it is allowed. If it is, the response is sent back to the frontend. The request is only allowed if the server considers it secure. This is achieved by checking the Origin header of the request. The server checks whether the value of the Origin header is included in a list of allowed values. If so, the request is allowed. Depending on the complexity of the request, a preflight request occurs, where a “preliminary” request with the OPTIONS verb is sent to check if the actual request is allowed.
For the services of the SU-TermServ, there are no restrictions that prevent requests from other servers.
However, in connection with mTLS, it is important to note that according to the specification, no TLS certificates are sent in the preflight request within the CORS mechanism. This leads to the server rejecting the request, as it is not considered secure. This behavior occurs in Firefox, as Firefox implements the specification correctly. In contrast, Chromium-based browsers send the certificates in the preflight request, which results in the request being considered secure.
Additionally, Firefox does not reliably send the certificates in the main request unless a corresponding setting is made in the JavaScript code. Since the applications Shrimp, Snapper, and OntoCommand were developed by CSIRO, this is currently not the case, but a corresponding adjustment is potentially being considered.
However, this behavior can be aligned with that of Chromium through a switch in the Firefox configuration. The setting network.cors_preflight.allow_client_cert should be set to true. This can be accessed via the URL about:config. After changing the switch, Firefox needs to be restarted. This setting also addresses both problems, so that the use of Firefox is possible without restrictions afterwards.
When you open the about:config page, a warning will appear:
Warnung when accessing about:config
Accept the warning and search for preflight. The setting network.cors_preflight.allow_client_cert should be set to false. Change the value to true by clicking on the symbol in the Value column. It should look like this afterwards:
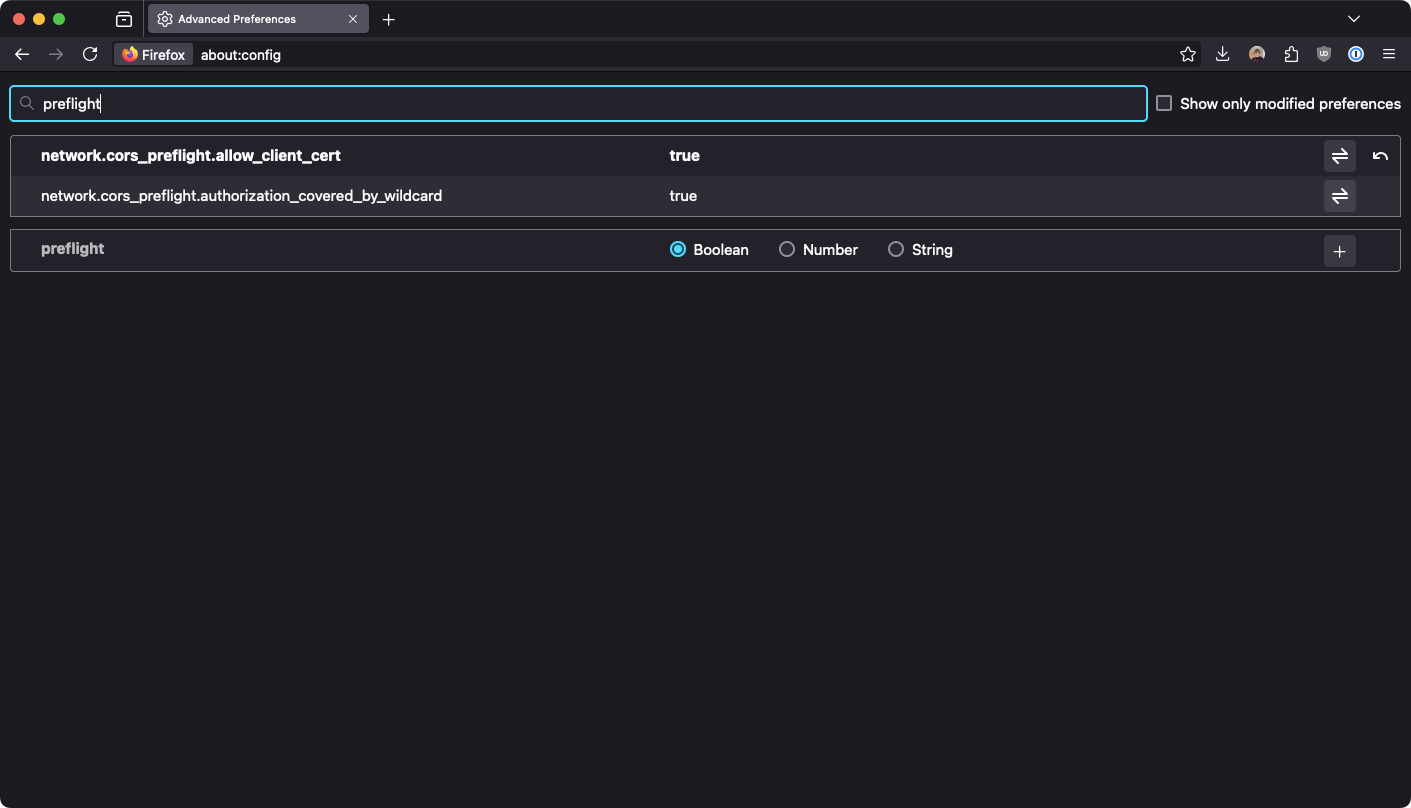
Warnung beim Aufrufen der about:config
Now, restart Firefox. To test the setting, access Shrimp. At least one certificate request should appear. If you confirm this, Shrimp should work as usual. For setting up the certificate, please refer to the corresponding FAQ entry.
